Cryptocurrency has transformed the financial industry, creating fresh opportunities for innovation and investment. However, with these advancements has come a surge of criminal activities, including scams, hacks, fraud, and ransom attacks. These threats undermine trust in the industry and pose risks to investors and institutions.
What is a Hack?
A hack occurs when unauthorized individuals access crypto wallets, exchanges, or blockchain networks to steal assets. The Ronin Network Hack (2022) and FTX Hack (2022) are prime examples, with $615 million and $400 million stolen.
What is Ransom?
Ransomware attacks involve malware that encrypts a victim’s data, demanding payment—usually in cryptocurrency—for decryption keys. A notable case is the 2021 Colonial Pipeline Attack, where hackers demanded $4.4 million in Bitcoin.
Common Scams in the Crypto Industry
Criminals in the crypto world often use various fraudulent tactics to deceive and exploit individuals and institutions. Here are some of the most common scams:
- Phishing Attacks: Scammers impersonate legitimate platforms, tricking users into revealing private keys or credentials. These attacks are currently the most prevalent method for stealing funds, accounting for a staggering 93.5% of all stolen cryptocurrency as of August 2024. For instance, a single phishing incident led to the loss of approximately 4,064 Bitcoin, valued at about $238 million.
- Ponzi Schemes: Fraudsters promise high returns on crypto investments, using funds from new investors to pay off earlier participants. A notable example is the collapse of Finiko, a Ponzi scheme that resulted in losses exceeding $1 billion. Participants were lured with promises of high returns, leading to significant financial damage when the scheme ultimately collapsed.
- Impersonation Scams: These scams can lead to millions in losses, though specific average amounts are less frequently reported and can vary significantly depending on the targets involved. Criminals often pose as well-known figures or organizations to solicit investments, tricking victims into parting with their money.
- MEV bot Scams: Fraudsters exploit MEV Bots or Trading Bots by promoting them as tools to generate easy profits. These bots are marketed as automated systems that capitalize on market inefficiencies, promising guaranteed returns. However, our blockchain investigations reveal that the actual intent is to siphon funds from victims to the scammers’ wallets.
- Rug Pulls: These scams occur when developers abandon a project after raising funds, leaving investors with worthless tokens. A notable example is the Thodex exchange incident, where users lost over $2 billion after the CEO vanished with the funds. Another instance is the AnubisDAO rug pull, which led to losses exceeding $58 million
Recent Scams in the Crypto Space
In August 2024, two men, Malone Lam and Jeandiel Serrano, were arrested by the FBI for their involvement in a cryptocurrency phishing scam that led to the theft of $230 million from a single victim in Washington, DC. The criminals posed as Google Support, tricking the victim into sharing their screen and resetting their two-factor authentication (2FA), which enabled them to access the victim’s private keys and steal 3,100 Bitcoin.
After the heist, the duo tried to launder the stolen funds through exchanges and mixing services, using peel chains to split transactions. Despite using VPNs and pass-through wallets to hide, authorities quickly identified them due to poor security practices. Their lavish spending on luxury cars, clubs, and designer goods also helped lead to their arrest.
This case underscores the importance of safeguarding private keys and 2FA credentials, as well as the risks of falling victim to social engineering scams in the crypto space.
How Are Stolen Funds Analyzed?
Stolen funds are typically routed through various wallet addresses or “tumblers” to obscure their origins. Lukka’s Blockchain Analytics can trace the flow of these assets, even through mixers, using proprietary tracking algorithms. It also offers automated risk scoring based on over 380 indicators, enabling institutions to evaluate the risks associated with suspicious crypto-asset addresses.
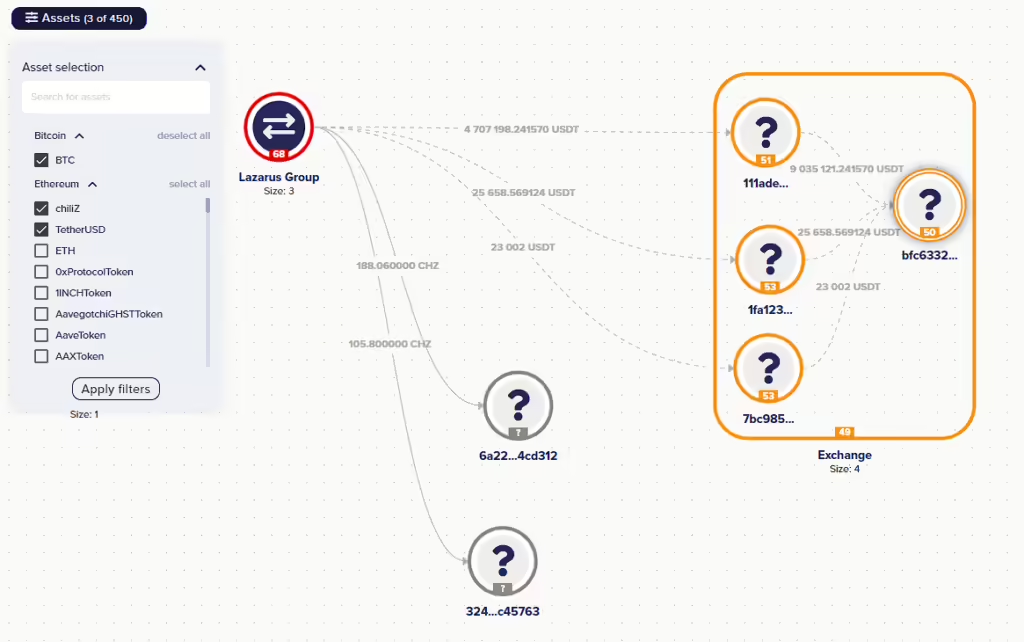
Understanding Draining and Poisoning in the Crypto Space
Draining is when someone illegally takes funds from a victim’s wallet or account, often through phishing or by exploiting weaknesses in smart contracts. Poisoning manipulates victims into thinking they’re dealing with a legitimate source, such as fake tokens or projects, ultimately leading to financial loss. Both methods take advantage of poor user awareness and security practices, highlighting the importance of education and vigilance in the crypto space.
Detecting and Preventing Scams and Fraud
Key Indicators of Scams:
- Unsolicited Offers: Promises of high returns or unexpected investment opportunities.
- Poor Website Design: Incomplete platforms with misspellings and unclear company information.
- Unverified Endorsements: Alleged connections to well-known individuals or companies without validation.
- Anonymous Developers: Projects lacking transparency about their team members.
- Suspicious Links: Phishing attempts often involve dubious URLs.
Staying Safe in the Crypto Space
To stay secure in the ever-growing world of cryptocurrency, individuals and institutions must adopt best practices:
- Use Trusted Platforms: Opt for exchanges and wallets with strong Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures.
- Enable Two-Factor Authentication (2FA): Adds an additional layer of protection to accounts.
- Secure Private Keys: Store keys securely and offline, preferably using hardware wallets.
- Research Thoroughly: Verify the legitimacy of new projects and review whitepapers carefully.
- Monitor Transactions: Lukka provides real-time monitoring and alert systems to detect suspicious transactions.
How Lukka Supports Investigations and Security
Lukka provides advanced tools, such as Blockchain Analytics and Blockchain Investigator, to track stolen funds, analyze transactions, and assist in recovering assets. Through proprietary clustering techniques, it aids law enforcement in tracing funds across blockchains.
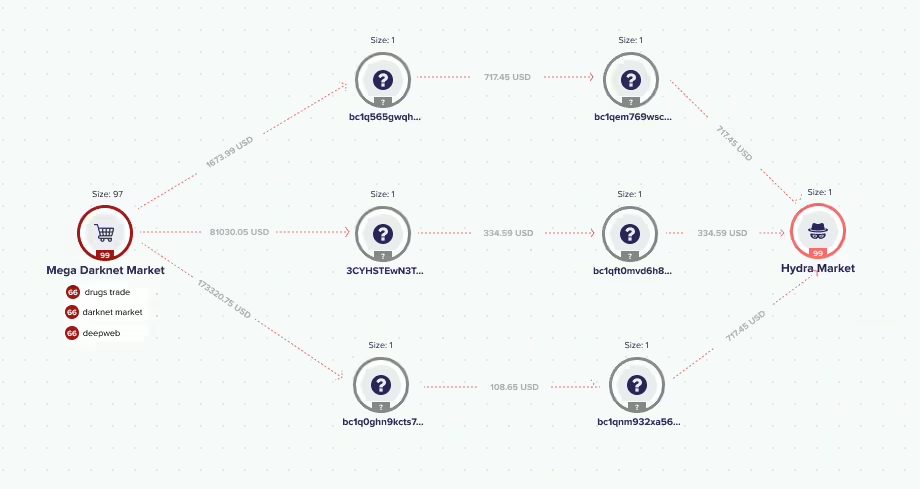
These tools assist companies in complying with regulations like MiCA by providing risk scoring, transaction monitoring, and forensic analysis to mitigate risks and maintain clear audit trails. With the rise in scams, hacks, and ransomware attacks, institutions must adopt strong security measures. Regulatory frameworks like MiCA promote transparency and investor protection, urging companies to implement advanced analytics and risk strategies.
Lukka’s solutions play a vital role in detecting fraud, ensuring compliance, and safeguarding the crypto ecosystem. In the face of growing cybercrime, these tools are essential for protecting users and staying ahead of emerging threats.


